Secure by Design. Resilient by Architecture.
Explore the iPU architecture built for defense-grade AI and edge intelligence—featuring embedded threat mitigation at the silicon level. From dynamic instruction routing to real-time attack surface minimization, this visual reveals how we integrate trust, performance, and protection into every layer of processing..
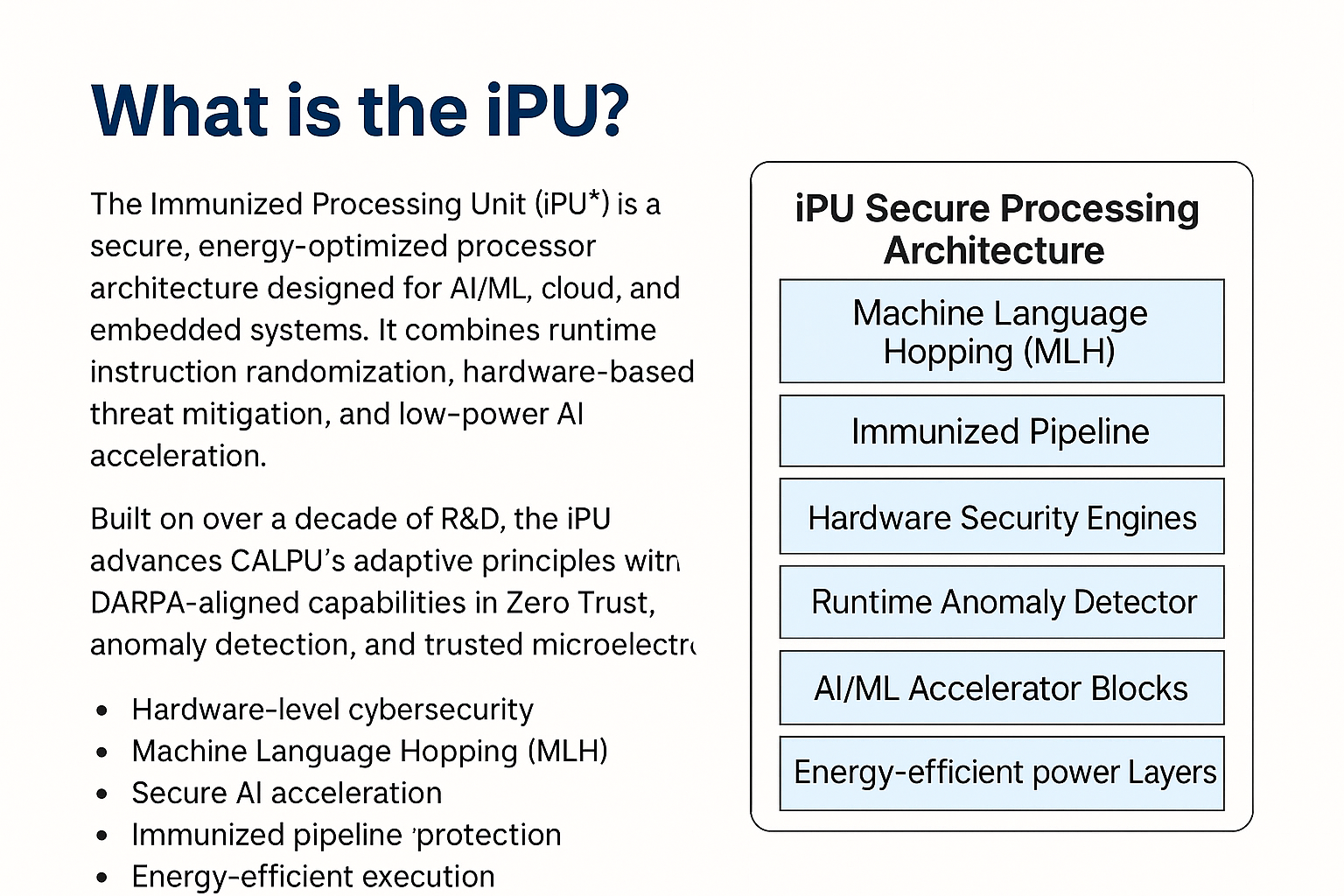
What is the iPU™?
🔹Intro:
The Immunized Processing Unit (iPU™) is a secure, energy-optimized processor architecture designed for AI/ML, cloud, and embedded systems. It combines runtime instruction randomization, hardware-based threat mitigation, and low-power AI acceleration.
Built on over a decade of R&D, the iPU advances CALPU’s adaptive principles with DARPA-aligned capabilities in Zero Trust, anomaly detection, and trusted microelectronics.
🔹 Highlights
Hardware-level cybersecurity
Machine Language Hopping (MLH)
Secure AI acceleration
Immunized pipeline protection
Energy-efficient execution
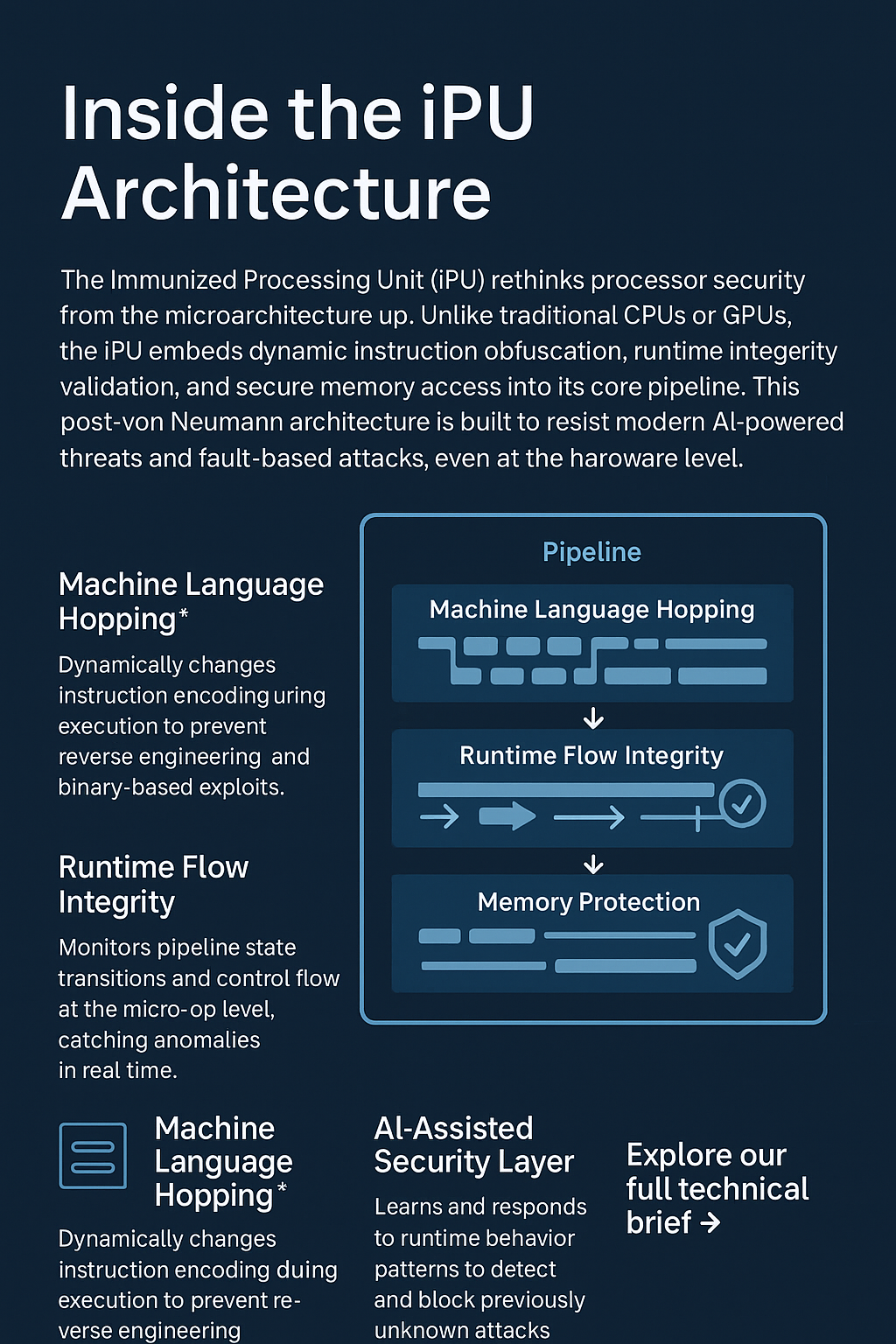
Inside the iPU Architecture
🔹 Intro:
The Immunized Processing Unit (iPU) rethinks processor security from the microarchitecture up.
Unlike traditional CPUs or GPUs, the iPU embeds dynamic instruction obfuscation, runtime integrity validation, and secure memory access into its core pipeline.
This post-von Neumann architecture is built to resist modern AI-powered threats and fault-based attacks, even at the hardware level.
🔹 3 Feature Callouts:
🛡️ Machine Language Hopping™
Dynamically changes instruction encoding during execution to prevent reverse engineering and binary-based exploits.
🔍 Runtime Flow Integrity
Monitors pipeline state transitions and control flow at the micro-op level, catching anomalies in real time.
🧠 AI-Assisted Security Layer
Learns and responds to runtime behavior patterns to detect and block previously unknown attacks.
Timeline
Immunized
Processing Unit Core
The Immunized Processing Unit (iPU) Core is a next-generation compute architecture that integrates runtime threat detection and response mechanisms directly into the silicon. Unlike conventional processor cores, the iPU Core employs an embedded "digital immune system" capable of identifying and neutralizing malicious behaviors, instruction anomalies, and side-channel activity in real time. Leveraging behavioral baselining, hardware-anchored integrity checks, and microcode-level containment, the immunized core delivers tamper-resilient computation across mission-critical AI and defense applications. This approach provides not just reaction—but proactive immunity, ensuring operational trust under adversarial conditions.
Machine Language
Hopping (MLH)
Machine Language Hopping (MLH) is a groundbreaking obfuscation and resilience technique that transforms the processor into a moving-target system by dynamically switching between diverse machine instruction sets during execution. This runtime polymorphism creates unpredictability at the binary level, significantly increasing resistance to reverse engineering, code injection, and persistent threats. MLH operates at the microarchitectural layer, abstracting the compute pipeline from any static attack surface. By continuously altering the execution landscape without interrupting application performance, MLH ensures that malicious actors face a non-deterministic and evasive target—ideal for secure embedded systems and next-gen military compute nodes.
Pipeline
Security Design
Pipeline Security Design introduces a hardened execution model within the iPU architecture, focused on minimizing vulnerabilities in instruction handling, scheduling, and memory access. This includes runtime verification stages, anomaly-tolerant registers, speculative execution monitoring, and secure branch resolution units—all embedded at the pipeline level. By embedding threat-aware logic throughout the execution flow, the design disrupts traditional exploit vectors such as timing attacks, instruction replay, and data leakage during speculative execution. The result is a resilient pipeline that maintains high performance while ensuring that every instruction is authenticated, validated, and securely executed—ideal for adversarial operational environments.
Hardware-Software
Co-Design Innovations
This architectural framework leverages tight coupling between hardware and software layers to optimize system performance, security, and adaptability in dynamic mission contexts. Through co-design, software can orchestrate hardware reconfiguration, while hardware enforces security policies with minimal latency and energy impact. Innovations include shared state models, trusted execution paths, and programmable microarchitectural controls that allow secure AI workloads to adapt in real time. This model eliminates the traditional abstraction barrier, enabling a responsive, collaborative computing fabric where software intelligence directly shapes hardware behavior—ensuring agility, trust, and mission-focused optimization across diverse deployments.
Upload Your Document
Submit your proposal, white paper, or technical brief in Word or PDF format. Our team will review your submission and respond promptly. Accepted file types: .doc, .docx, .pdf